Cybersecurity Maturity Model Certification (CMMC) is the culmination of over 5 years of tremendous efforts made by experts from NIST, DoD, MITRE and others, to protect the Defense Industrial Base (DIB) Sector from cyber-attacks originating from adversaries targeting the DoD and its supply chain of prime and sub-contractors down to the 8th level, located within and outside of the continental United States, totaling over 350,000 entities.
What makes CMMC so unique?
1. CMMC takes security beyond compliance.
2. CMMC is not a one-size-fits-all Cybersecurity certification.
3. CMMC requires 100% conformity to practices and processes.
4. CMMC is a continuous improvement process for Cybersecurity.
5. CMMC is the first multilevel maturity-based Cybersecurity certification.
The evolution of Cybersecurity certifications
In the past 2 decades, Cybersecurity certifications have evolved as much as the cyber threat landscape.
To highlight this evolution, I decided to turn to one of the trusted sources available to us on the Internet, Wikipedia.
Visa CISP of 2001 was superseded by PCI-DSS in 2004
According to Wikipedia:
“The Cardholder Information Security Program (CISP) was a program established by Visa USA in 2001 to ensure the security of cardholder information as it is being processed and stored by merchants and service providers.
As of 2004, CISP has been superseded by the PCI Data Security Standard, a multi-vendor initiative to tackle Payment Card Industry security issues.”
Sarbanes–Oxley Act of 2002 spurred SOC 1, SOC 2 and SOC 3
According to Wikipedia:
“In 2002, Sarbanes-Oxley was named after bill sponsors U.S. Senator Paul Sarbanes (D-MD) and U.S. Representative Michael G. Oxley (R-OH). As a result of SOX, top management must individually certify the accuracy of financial information. In addition, penalties for fraudulent financial activity are much more severe. Also, SOX increased the oversight role of boards of directors and the independence of the outside auditors who review the accuracy of corporate financial statements.”
“System and Organization Controls (SOC), defined by the American Institute of Certified Public Accountants (AICPA), is the name of a suite of reports produced during an audit. It is intended for use by service organizations (organizations that provide information systems as a service to other organizations) to issue validated reports of internal controls over those information systems to the users of those services. The reports focus on controls grouped into five categories called Trust Service Principles. The AICPA auditing standard Statement on Standards for Attestation Engagements no. 18 (SSAE 18), section 320, “Reporting on an Examination of Controls at a Service Organization Relevant to User Entities’ Internal Control Over Financial Reporting”, defines two levels of reporting, type 1 and type 2. Additional AICPA guidance materials specify three types of reporting: SOC 1, SOC 2, and SOC 3.”
British Standards (BS) 7799 of 1995 was superseded by ISO/IEC 27001 in 2005
According to Wikipedia:
“BS 7799 was a standard originally published by BSI Group in 1995. It was written by the United Kingdom Government’s Department of Trade and Industry (DTI), and consisted of several parts.
The first part, containing the best practices for information security management, was revised in 1998; after a lengthy discussion in the worldwide standards bodies, it was eventually adopted by ISO as ISO/IEC 17799, “Information Technology – Code of practice for information security management.” in 2000. ISO/IEC 17799 was then revised in June 2005 and finally incorporated in the ISO 27000 series of standards as ISO/IEC 27002 in July 2007.
The second part of BS7799 was first published by BSI in 1999, known as BS 7799 Part 2, titled “Information Security Management Systems – Specification with guidance for use.” BS 7799-2 focused on how to implement an Information security management system (ISMS), referring to the information security management structure and controls identified in BS 7799-2. This later became ISO/IEC 27001:2005. BS 7799 Part 2 was adopted by ISO as ISO/IEC 27001 in November 2005.
BS 7799 Part 3 was published in 2005, covering risk analysis and management. It aligns with ISO/IEC 27001:2005.”
Certifications take security beyond compliance
In one of my earlier thought leader articles published in the November 2006 edition of the ISSA Journal, titled ISO/IEC 27001: The future of infosec certifications, I emphasized that ISO/IEC 27001 certification allows organizations to build an effective Information Security Program that addresses current and future regulatory compliance requirements in a sustainable and cost-effective fashion.
I did not have a crystal ball in my hands when I wrote this article almost 15 years ago, but somehow my prediction has indeed come true.
Compliance ≠ Security, especially in Cyberspace!
I always emphasize in my public speaking engagements and when teaching the HISP Certification Course, that we can take a lesson from history through the sinking of the Titanic. The Titanic was meant to be an unsinkable cruise ship; they checked all the boxes from a compliance standpoint, such as the maximum passenger and crew capacity, number of lifeboats required and occupancy limits, but they failed to perform a through risk assessment.
Compliance should be seen as a starting point and not the be all, end all to achieve effective cyber risk mitigation.
Now, I can categorically state that the future of infosec certification is to take security beyond compliance.
Certifications should not be a one-size-fits-all
Certifications are meant as an objective, impartial, independent assessment of a professional or other entity’s conformity to a given standard, framework or sets of requirements. CMMC is not a one-size-fits-all certification.
There are so many dependencies during a certification process (scope, maturity, location, assessor competency etc.) that makes it impossible to do a true apples-to-apples comparison of the security postures of two certified entities, so taking a one-size-fits-all approach to certifications is not only misleading, but could give a false sense of the true security posture of an entity, so a one-size-fits-all approach to certifications is fundamentally flawed.
Certifications should require 100% conformity
Cybersecurity Certifications have traditionally not required 100% conformity; the current cyber threat landscape and increasing threats from nation states targeting the DoD DIB require a different approach to certifications.
Come to think of it, most US residents are required to take their vehicle for an emission test once a year, to prove its road worthiness. These tests require 100% compliance and so should data worthiness.
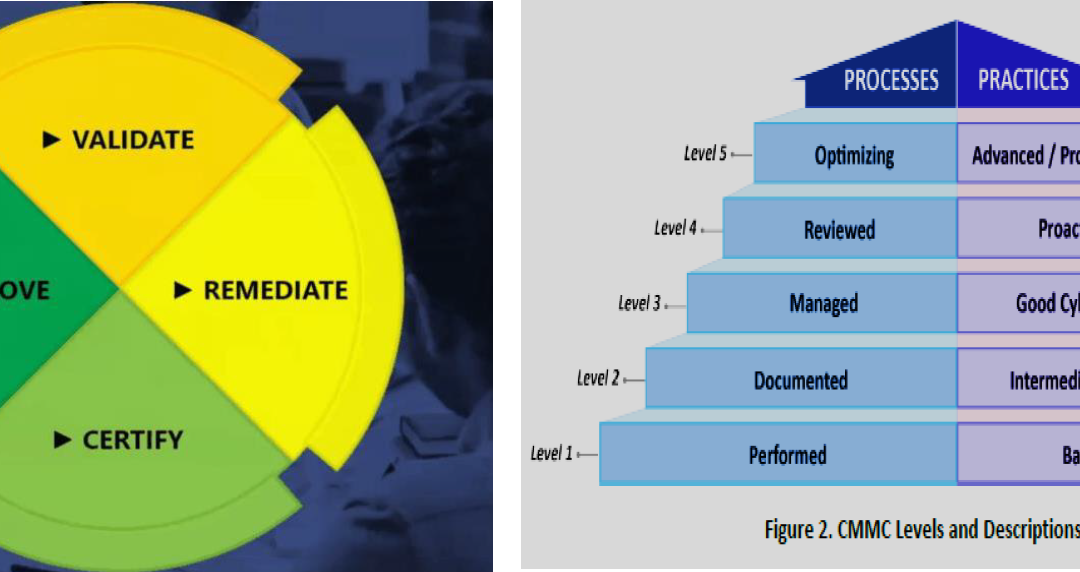
CMMC provides 5 cumulative maturity levels, each requiring a set of processes and practices to be fully implemented and operationalized. An Organization Seeking Certification (OSC) may choose to initially pursue Certification to Maturity Level 1 by implementing 17 practices. Once this initial milestone is achieved, they can then incrementally adopt the additional practices required to achieve certification to higher Maturity Levels.
Certifications should be a process for continuous improvement
Cybersecurity is a journey and not a destination, right? So, why do organizations just stop at certification?
Going back to my previous point about us taking a lesson from the Titanic, built to be an unsinkable cruise ship, Compliance + Continual Improvement Process through ongoing Risk Assessments would have identified the need for protection against physical factors, such as weather and ICEBERGS!
CMMC allows organization to embrace a continuous improvement process by incrementally pursuing improvements from one level maturity to the next in a cumulative manner.
According to Wikipedia:
“A continual improvement process, also often called a continuous improvement process (abbreviated as CIP or CI), is an ongoing effort to improve products, services, or processes. These efforts can seek “incremental” improvement over time or “breakthrough” improvement all at once. Delivery (customer valued) processes are constantly evaluated and improved in the light of their efficiency, effectiveness and flexibility.”
“The PDCA (plan, do, check, act) or (plan, do, check, adjust) cycle supports continuous improvement and Kaizen. It provides a process for improvement since the early design (planning) stage of any process, system, product or service.”
Certifications should be multilevel maturity-based
CMMC stands on its own by taking a multilevel maturity-based approach to certification that inherently embraces the concept of continuous improvement.
According to Wikipedia:
“Maturity is a measurement of the ability of an organization for continuous improvement in a particular discipline (as defined in O-ISM3). The higher the maturity, the higher will be the chances that incidents or errors will lead to improvements either in the quality or in the use of the resources of the discipline as implemented by the organization.
Most maturity models assess qualitatively people/culture, processes/structures, and objects/technology.
Two approaches for implementing maturity models exist. With a top-down approach, such as proposed by Becker et al., a fixed number of maturity stages or levels is specified first and further corroborated with characteristics (typically in form of specific assessment items) that support the initial assumptions about how maturity evolves. When using a bottom-up approach, such as suggested by Lahrmann et al., distinct characteristics or assessment items are determined first and clustered in a second step into maturity levels to induce a more general view of the different steps of maturity evolution.”
Potential of CMMC beyond DoD’s DIB Sector
CMMC gets rolled out to the DoD DIB over the next 5 years. Its impact on the following will become more apparent and is worth paying attention to, so I intend to write about these in future posts, so watch this space!
1. Cyber Liability Reduction
2. Cyber Insurance Discounts
3. Breach Probability Prediction
4. Breach Probability Reduction
5. Cybersecurity Program Effectiveness
If you need a partner in your CMMC Journey, schedule your FREE 30 minute advisory call with me here.
Otherwise, have fun embracing CMMC As A Process for Continuous Improvement!
Regards,
Taiye.

Recent Comments